
Nigerian Hacker Exposed: AI, Infrastructure, and Love
At CyberArmor, our DarkArmor platform collected and analyzed over 3,000 screenshots from a Nigerian cybercriminal’s desktop. What we uncovered goes far beyond the outdated image of “419 scams.” Today’s threat actors operate with sophistication, leveraging AI tools, stolen infrastructure, and even personal networks to run cybercrime like a modern business.

How a Nigerian Hacker Uses AI to Build Cybercrime Tools and Launch Phishing Attacks
Recently, DarkArmor Platform collected and analyzed over 3,000 screenshots from the desktop of a Nigerian-based cybercriminal. These screenshots provide a rare, behind-the-scenes look into the daily operations of a modern threat actor—revealing not only how campaigns are built and executed, but also how commercial AI platforms like ChatGPT and Grok
Phishing Attack Targets Canadian Infrastructure on Canada Day
This Canada Day, while the country celebrates its national pride, cybercriminals launched a widespread phishing campaign targeting key sectors across Canada. The attack, observed early this morning, focused on industries critical to the nation’s infrastructure, including construction engineering, energy, plumbing, and public utilities. Overview Our systems detected a coordinated phishing
Threat Insight: Cybercriminals Abusing Vercel to Deliver Remote Access Malware
CyberArmor has identified a phishing campaign leveraging Vercel, a legitimate frontend hosting platform, to distribute a malicious version of LogMeIn — a legitimate remote access tool — used by cybercriminals to gain full control over victims’ machines. Phishing Technique Cybercriminals sent phishing emails containing a link that directed recipients to
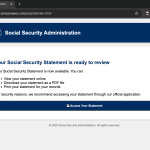
Hacker Exploit Social Security Statement Theme to Target Over 2,000 Victims with Malware
In a recent campaign uncovered by CyberArmor analysts, cybercriminals exploited the theme of official Social Security statements to deceive over 2,000 individuals into downloading malware. The attack involved a highly convincing phishing lure designed to appear as a legitimate communication from the Social Security Administration (SSA). Figure 1 shows the

Uncovered: How Cybercriminals Scam Each Other Using Fake USDT Sender Software
Overview Infostealers have become a significant threat in recent years, with their prevalence increasing daily. In this blog, we uncover how cybercriminals exploit legitimate software to socially engineer users into downloading and executing malicious programs. Once launched, the software takes full control of the user’s machine. Figure 1 provides an

